
Navigating the complexities of online data management, businesses face a crucial challenge: ensuring the security of their data in the cloud.
45% of breaches are cloud-based. According to a recent survey, 80% of companies have experienced at least one cloud security incident
With the increasing reliance on cloud services, the risk of data breaches and unauthorized access has escalated, making cloud computing security not just a technical issue but a vital business imperative.
| As Jeffrey S. King, President of AT-NET, says, “Prioritizing cloud security is non-negotiable; it’s critical to safeguarding our data and ensuring operational resilience.” |
In this blog, we’ll understand what is cloud security and explore effective strategies to safeguard your data and infrastructure in the cloud.
What is Cloud Computing Security?
It’s a subset of computer security specifically focused on safeguarding cloud computing environments against unauthorized access, data breaches, and other cyber threats.
This form of security is critical because it deals with the protection of data, applications, and infrastructures involved in cloud computing.
Source: Norton
What is Cloud Security Threats?
These threats encompass a range of issues, including compromised credentials, broken authentication, hacked interfaces, and data breaches. They pose a significant risk to organizations using cloud services.
According to Statista, the top cloud security concerns are data loss and leakage (69%), and data privacy/confidentiality (66%), followed by accidental exposure of credentials (44%).
Concerned About Data Safety in the Cloud?Trust AT-NET to fortify your cloud environment against threats. |
The Importance of Cloud Computing Security
Cloud computing security is vital for several reasons. First, it protects sensitive data from unauthorized access and cyberattacks. With the increasing amount of data stored in public clouds, the need for robust security measures has never been more crucial.
Additionally, cloud security solutions help maintain compliance with various regulatory requirements. Many industries have specific guidelines for data protection and privacy, and cloud security helps organizations adhere to these standards.
Source: Norton
What is Infrastructure Security in Cloud Computing?
Infrastructure security in cloud computing involves protecting the fundamental components, such as servers, storage, and networking, that make up the cloud environment. This is essential for maintaining the integrity and availability of data and applications hosted on cloud platforms.
What is Cloud Workload Security
It refers to protecting the computational tasks and processes that run in a cloud environment. Ensuring these workloads are secure is vital to prevent malicious activities that could compromise the entire cloud infrastructure.
What is Data Security in Cloud Computing
Data security in cloud computing is another critical aspect that involves protecting data at rest, in transit, and in use. It encompasses measures to prevent data breaches and loss, ensuring the confidentiality, integrity, and availability of data.
Understanding Security Controls in Cloud Environments
Security controls in a cloud environment are the measures and technologies used to protect data, applications, and infrastructure.
These include access controls, encryption, intrusion detection systems, and other mechanisms that enhance the security posture of cloud computing environments.
Cloud Service Models and Security
The two popular cloud service models, Software as a Service (SaaS) and Infrastructure as a Service (IaaS), each have unique security considerations.
- SaaS applications, like Microsoft Azure, often come with built-in security features, but it’s essential to understand the security responsibilities shared between the service provider and the user.
- In contrast, IaaS offers more control over infrastructure but also demands a higher level of security management from the user.
The Correlation Between Hybrid Clouds and Security Challenges
Hybrid clouds combine public and private cloud elements, bringing unique security challenges. Ensuring seamless security across diverse environments while maintaining data protection and preventing unauthorized access is crucial in hybrid cloud setups.
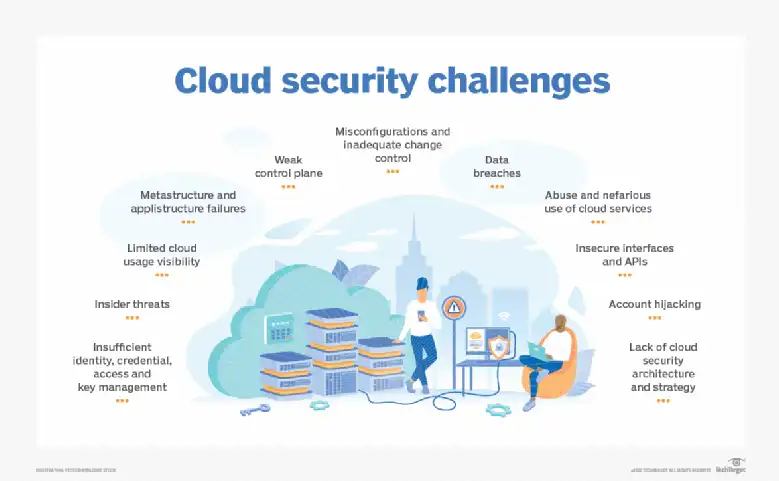
Mitigating Security Issues in Cloud Computing
To address security issues in cloud computing, organizations must implement comprehensive security measures. This involves setting up
- Strong access controls
- Regulate access to sensitive data
- Incorporate APIs
- Remain compliant with regulations
- Using encryption to protect data
- Regularly updating & patching systems
- Conducting continuous security monitoring
| More resources you might like: Why is Network Security Important?Top 8 IT Procurement Best Practices |
Why is it Important to Have Responsibility for Cloud Security?
Understanding security responsibilities in the cloud is key. In cloud computing, both the service provider and the user share security responsibilities. While providers are responsible for securing the infrastructure, users must protect their data and applications.
Cloud Security Best Practices for Businesses
| Best Practice | Description | Benefits |
| Regular Security Audits | Conducting periodic evaluations of security policies and systems | Identifies vulnerabilities, ensures compliance |
| Data Encryption | Encrypting data both at rest and in transit | Protects sensitive information, prevents breaches |
| Strong Access Controls | Implementing robust user authentication and authorization mechanisms | Limits unauthorized access, enhances data security |
| Employee Training | Regular training sessions on security protocols | Reduces risk of human error, increases awareness |
| Multi-Factor Authentication | Using additional verification steps for accessing cloud services | Strengthens login security, mitigates risk of compromised credentials |
| Regular Software Updates | Keeping all software and security tools updated | Protects against the latest threats, maintains system integrity |
| Disaster Recovery Planning | Establishing procedures for data backup and recovery | Ensures business continuity, minimizes downtime in crisis |
| Vendor Risk Management | Assessing and managing risks associated with third-party vendors | Safeguards against third-party vulnerabilities, maintains supply chain security |
Safeguard Your Cloud Environment With AT-NET
As we delve into the complexities of cloud computing security, the pivotal role of experienced service providers becomes unmistakable.
AT-NET brings 25 years of deep-rooted experience in cloud security, coupled with a forward-thinking approach, that offers businesses not just solutions but a strategic partnership in securing their cloud environments.
| Learn More About Our Cloud Services Near You: |
In a world where cyber threats are ever-evolving, and data security is paramount, aligning with our seasoned expertise means embracing a future where cloud security is no longer a challenge but a well-managed asset driving business growth and innovation.
With our expertise at your service, you can concentrate on advancing your business, assured that your cloud security is in capable hands.
Reach out to us, and together we’ll transform cloud security challenges into a safeguarded future for your business.



