Log 4 Java
Within the last few weeks a new and extremely serious Java vulnerability has been discovered, Log4J.
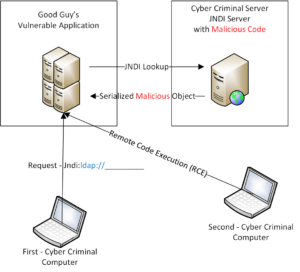
This is very dangerous because it can allow Remote Code Execution (RCE). Remote code execution can allow almost anything to be placed or launched in systems with this vulnerability. If most of the below does not make sense, I have drawn a diagram that I think will help before you read my explanations.
There are three items I need to explain in order for one to understand the issues:
Number 1
- The Logging Library for Java (Log4J) is open source code and anyone can manipulate or inspect the code.
- The library store objects in a serialized fashion; meaning that you can insert code in the logs.
- Cisco makes extensive use of Java for its products (side note)
- The Log4J library is popular and if you have code that runs Java then you probably have the vulnerability. Synk indicates that if you have a Java app the 38.2% of the normal applications use the library. If you have not installed the library but purchased module then 60.8% of applications probably have the code. What this means is that you need to patch your code, ASAP.
- The Common Vulnerability Scoring System (CVSS) rates this exploit as a “10”, Critical. A CVSS score is composed of three sets of metrics (Base, Temporal, Environmental), each of which have an underlying scoring component.
- This vulnerability also is also deemed as and RCE (Remote Code Execution) hack. This means that any malicious code can be inserted in to your systems and allow someone to take over control of the system.
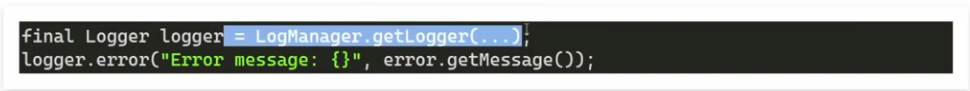
- Below is a simple Logger construct
Number 2
- JNDI (Java Naming and Directory Information) stores Java Object in a serialized fashion. The key here is “Directory Information”, private stuff.
- Java is backward compatible and has a mandate to make old and new systems work together. This means “openness” and exposure.
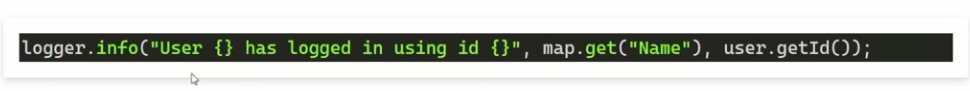
- Below is the logger getting a user name.
Number 3
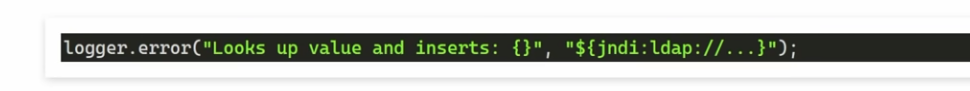
- Any valid “string” like an LDAP lookup with a URL can be passed to Java
- Below is a code example. Note the the ldap:// can be pointed to a malicious server through your application.
- Upon return from malicious server, a Java Object (evil code) is inserted into the log. Voila!, cyber criminals have control of your systems.
I know the above is a lot for a blog but if you need a verbal explanation, call me (844) 506-2116 and I will help. We can also check your systems to see if they need patching and check out our Managed Services offerings.
created by Jeff King (Linkedin – Jeff King)

