
You’ve likely heard a lot of news regarding the importance of creating stronger passwords. According to Verizon’s 2022 Data Breach Investigations Report, 81% of hacking-related data breaches were the direct result of weak or stolen passwords. There is more than one way to protect your passwords, and that raises the question about MFA vs. 2FA.
Furthermore, the same report indicates that 75% of breaches were caused by outside attackers, while 25% happened from within. These situations have forced many businesses to ask themselves how strong their passwords truly are.
Single factor authentication for logging in to gain access to company data is no longer an effective means of protection. As a result, many organizations now require multiple factors of authentication to verify user identity and improve access management.
Two options exist for better user authentication: Multi-Factor Authentication (MFA) and 2-Factor Authentication (2FA). In this article, we’ll examine the differences between MFA vs. 2FA, and why strong authentication is required for today’s businesses.
Develop a Multi-Factor Authentication Policy With a Proven PartnerImplement an MFA solution for your business with AT-NET’s cybersecurity services. |
What Does MFA Mean?
Many small businesses wonder “what does MFA stand for?” Let’s begin by exploring the answer to that question.
The MFA acronym is short for Multi-Factor Authentication. It consists of multiple steps required for user authentication when logging into password-protected software or applications. Each step requires users to perform a different form of user identity verification.
This authentication method generally adheres to the following format, but can sometimes consist of additional steps:
- A user attempts to log into the corporate VPN where critical company data is housed.
- They type their username and password into the login screen and press Enter.
- Instead of gaining direct access to the VPN, an extra window appears that requires the user to enter a numeric code – usually five or six characters long – that is sent to their mobile phone.
- If the user is the rightful owner of the credentials, they’ll receive this code via text message and push notification, enter it into the pop-up window, and gain access to the VPN.
Depending on the company, the industry it operates within, and the sensitivity of the data, additional factors of authentication may be required as a means of increasing security. These methods include, but are not limited to:
- Retina scans
- Facial recognition
- Thumbprint scans
These extra methods can effectively transform a 2FA strategy into a full-fledged MFA solution while preventing unauthorized access that leads to data breaches and theft.
MFA vs. 2FA: Understanding the Differences
While either authentication method is effective for safeguarding your data, the primary difference between 2FA vs. MFA is the amount of additional forms of user authentication required.
As its name suggests, 2-Factor Authentication (2FA) only includes one extra layer of authentication. In most cases, this is generally a one-time password or numerical code.
Multi-Factor Authentication (MFA), on the other hand, can feature as many as four additional user identity verification methods. These can include retina scanning, fingerprint scanning, and facial recognition.
The most notable MFA benefit that makes it a more attractive option over 2FA is the extra layers. Despite that, even if you choose to go the 2FA route, your business still has double the amount of protection over single factor authentication.
Why is MFA Important for Small Businesses?
There are several reasons why having multiple factors of authentication in place is important for today’s small and medium-sized businesses:
- MFA and 2FA provide additional layers of access management. This is especially beneficial if the credentials are protecting extremely sensitive client, corporate, or personal information where strong authentication is required.
- They are required in order to meet cyber insurance policy requirements. When you apply for a cyber insurance policy for your business, insurers will require you to have a functional multi-factor authentication policy in determining your eligibility for coverage.
- They help you prevent data breaches and cyber attacks. Whether you choose 2FA vs. MFA, both are effective at protecting your businesses from attacks executed by automated sources, systematic password guessing, wide nets, or bot activity.
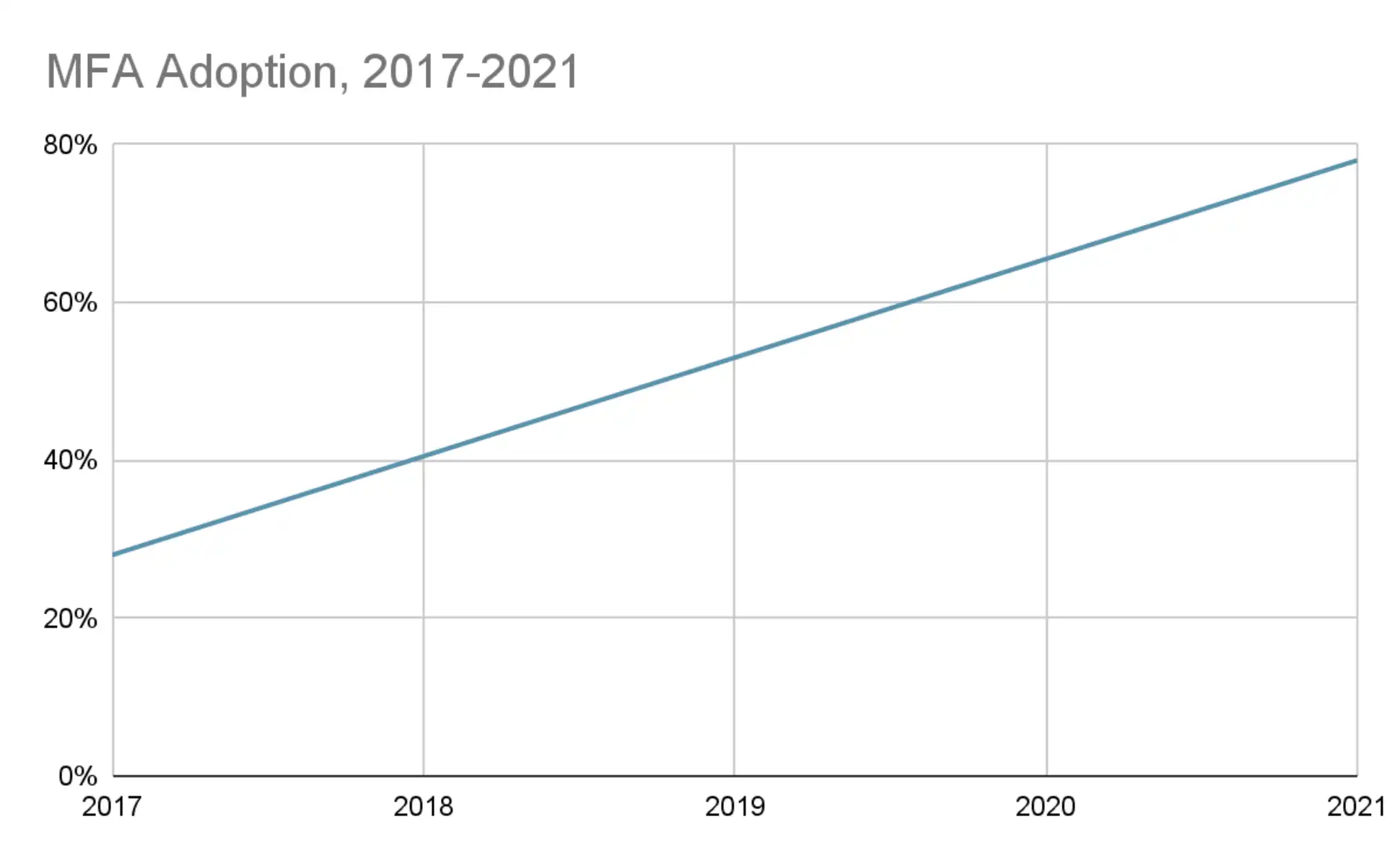
These benefits are significant, which resulted in a 178% increase in MFA solution adoption between 2017 and 2021.
How a Multi-Factor Authentication Policy Enhances Your User Experience
There are definitely merits to utilizing either a 2FA or MFA solution for your business. However, just like any other new policy you implement, MFA requires some adjustment from your staff.
They may find it annoying or even redundant at first, especially if frequent push notifications are part of your user authentication strategy. This leads to what is known as MFA fatigue, and can potentially leave your business and its data vulnerable to MFA fatigue attacks.
It may take some time, but your employees will eventually come to accept and even appreciate the fact that your company has a robust multi-factor authentication policy that can block an impressive 99.9% of automated cyber attacks and data breaches.
Interested in learning more about MFA vs. 2FA and data protection? Check out these blogs:
|
2FA vs. MFA: Make the Right Choice for Your Business
Now that you understand why MFA and 2FA are instrumental for increasing security and regulating access management, you may be wondering how to implement a multi-factor authentication policy of your own.
As an experienced managed services provider specializing in cybersecurity, AT-NET can help you understand the benefits of MFA vs. 2FA, in addition to helping you implement the authentication method that best aligns with your business’s data security needs.
Get in-depth insight into why strong authentication is required for survival in today’s evolving threat landscape by contacting us today to schedule a free consultation with our team of digital security experts.

