Physical Security and Cybercriminals
Question from one of our readers; Can bad physical security thwart good cyber security? The answer is simple, any security shortcuts will leave one vulnerable. We always tell customers; It is not if you will be breached by cybercriminals but how will you handle the breach when it occurs. We follow, at a minimum, the NIST 800-171 V2 standards for cybersecurity? The NIST 800-171 standards require access controls and logging for guests, employees, vendors and anyone coming in contact with Controlled Unclassified Information (CUI).
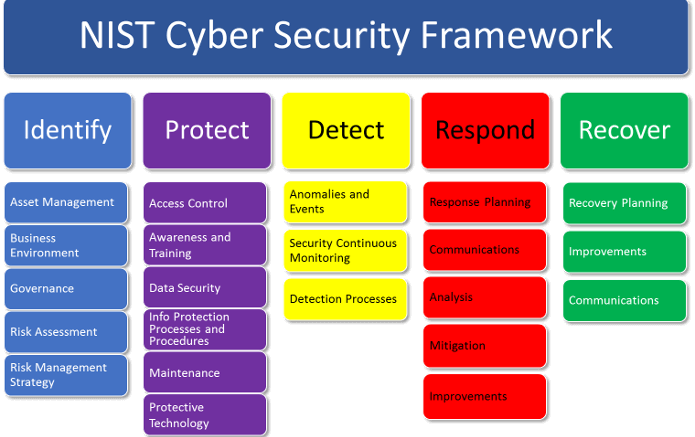
As an example think of a single room with one important file folder in the room. The room needs to be locked and only select people need a key to the room. The keys need to be controlled and the key holders need to be controlled. When one of the key holders enter the room to manipulate the file they need to be watched and logged (recorded). Just because the person entering the room was once trusted does not mean the the person can be trusted forever. There are five ideas to keep in mind when developing a security stance: Identify, Protect, Detect, Respond, and Recover. One also must have a process (policy) to detect wrong doing to the file. One also has to know how to respond to the potential unauthorized actions. Finally, how will you be able to recover from any breach. The before mentioned ideas are covered under each requirement from NIST 800-171. The below chart will help one create an idea of the requirements.
When we review customers cybersecurity stance, we very frequently find that there are three main deficits: physical security, policies, and SIEM.
Physical Security
Physical Security can be summarized as monitoring, logging, and controlling access to areas with CUI. Door access control through the used of Biometrics or Key fobs with access codes is a very good way to eliminate the use of physical keys. Physical keys can be easily copied or stolen. One also need to have cameras at ingress/egress locations. The cameras must be able to clearly see people coming and going for identification purposes. Visitors must also be escorted and logged when entering the building which contains CUI.
Polices
Almost all customers who engage AT-NET on cybersecurity initiatives do not have any type of policies at the start of our engagement. Polices have to be developed, updated, read, understood and adopted by all employees with interaction around or directly with CUI. Below is not an exhaustive list but is where we start creating policies for customers with cybersecurity requirements:
- Acceptable Use Policy
- Anti-Virus and Malware Policy
- Asset Management Policy
- Change Management Policy
- Code of Ethics Policy
- Corporate Policy Program
- Data Access and Password Policy
- Data Back-up Policy
- Data Classification Policy
- Data Retention Policy
- Encryption Policy
- Facility Security Policy
- HR Corrective Action Procedure
- Human Resource Security Policy
- Information Security Committee Policy
- Information Security Risk Assessment Policy
- Interconnection Agreement Policy
- Logging and Monitoring Policy
- Perimeter Security and Administration Policy
- Policy or Standard Exception Request Form
- Policy or Standard Exception Request Procedure
- Policy or Standard Variance Request Form
- Policy or Standard Variance Request Procedure
- Security Incident Response Policy
- Service Provider Security Policy
- Software Development Policy
- System Configuration Policy
- Telecommuting Assignment
- Telecommuting Policy
- Telecommuting Self-Certification Safety Checklist
- Vulnerability Identification and System Updates Policy
SIEM
Simply, SIEM, is the ability for software to determine cyber anomalies in real-time. We are huge fans of implementing SIEM
for every customers. SIEM, in my opinion, is a staunch requirement for all modern day businesses.
SIM (security information management) and SEM (security event management) are an interrelated set of practices that are referred to together as SIEM. SIM focuses on collecting a wide range of log data, which is useful for cyber forensics, internal security audits, and compliance reporting. On the other hand, SEM focuses on analyzing and correlating log data in real-time to find anomalies and improve threat response. These tools can offer advanced visualization, real-time awareness, and automation of IT operations.
As always, if you have questions call us at 844-506-2116 and we can help improve your cybersecurity posture!
Just so you know about AT-NET Services…
The Best MSP Professionals and Cybersecurity Professionals
Flat Fee IT Service, HIPAA, PCI, SEC, FINRA Services, Business Risk Management Services. IT Project Management, Managed IT Services, Co-Managed IT Services, Cloud Solutions, VoIP Solutions ,IT Helpdesk, Workstation Support, Windows Server Support, Cybersecurity Solutions, Vulnerability Management ,Network Infrastructure, Email Security, Data Backup & Recovery, Phishing Simulation. Security Awareness Training, Security Risk Assessments, Microsoft 365, Security Cameras, Integrated Door Access, and Structured Cabling.
created by Jeff King (Linkedin – Jeff King)